The digital age has revolutionized how we do business, communicate, and share information, opening up incredible opportunities. Yet, as our dependence on technology increases, so does the sophistication of cyber threats. Phishing is among the challenges we face. Cybercriminals are resourceful in fraud scenarios, hunting for your money and personal data, and it’s crucial to be aware of these threats and ensure our systems are well-protected.
In recent years, electronic signatures have gained immense popularity for their efficiency and convenience. They make life easier, enabling professionals to gather signatures on any document in minutes and significantly save time on paperwork completion. Over more than a year, their adoption across various industries has grown, but the risk of scammers imitating eSignature service emails to steal personal or financial data has also increased.
Phishing attacks can target organizations of any size, often using mass emails to exploit even a small open rate for profit. Often, such letters contain fillable fields for payment details or unprotected URLs leading to websites where visitors are supposed to create a new account and log in to the system. The scenarios vary. The good news is that you can thwart such attacks by implementing a dependable document signing solution. By managing a reliable platform, users can safeguard their transactions against fraudulent activities.
In this article, we will unveil the types and common traits of email fraud, examine examples of spam emails users might receive from eSignature providers, discuss prevention strategies, and highlight what makes SignNow a truly reliable service for online document signing.
What is phishing?
According to Wikipedia, phishing is a form of social engineering and a scam in which attackers deceive people into revealing sensitive information or installing malware, such as viruses, worms, adware, or ransomware. It’s a cybercrime that aims to lure users out of their personally identifiable details, credit card details, financial information, and passwords, resulting in ID thefts and money losses. According to IBM, scam emails account for 41% of all cyber threats globally.
Phishing uses manipulation and deception. The attackers pretend to be trustworthy entities to trick people into taking action. For example, they may ask for your account password, encourage you to click on fake websites with hidden fees, download files containing viruses, or reveal sensitive information like bank accounts and credit card details.
How a phishing email works
The term “phishing” comes from the mid-1990s, when hackers used misleading emails to “fish for” information from unsuspecting users. Since then, fraudsters have become more inventive, and their attacks have become more complex and sophisticated. Let’s see what types of internet attacks are popular now.
Types of phishing attacks
Cybersecurity threats vary, and as technologies develop, more ways to cheat people on the internet arise. Here are the most popular types of internet frauds you should know about:
- Email phishing
This is the most common form of cybercrime when attackers send mail that looks legitimate but, in reality, misleads users into clicking on a malicious website link or entering their personal or banking information.
- Spear phishing
Such attacks focus on specific individuals, such as a company’s system administrator, to steal login credentials. Attackers typically gather detailed information like the individual’s name, position, and contact details before initiating the attack.
- Whaling
It’s another form of spear phishing that targets “bigger fish” (the so-called whales)—the CEO, CFO, and other key people in a company.
- Vishing
This type of fraud refers to a voice call from someone pretending to be a representative of a trustworthy organization and asking to provide credit card or bank account details in order to fix some issues.
- Smishing
This kind of attack uses SMS to steal banking information. The text messages look like those you get from your bank telling you to navigate the given link and verify your account. This gives the fraudsters control over your finances and leads to direct money loss.
These attacks differ in scenarios, but their purpose remains the same—to cause harm and steal money and data. Knowing how to recognize such deceptions is one way to protect yourself. Let’s focus on the typical characteristics of the scams you may get by mail.
General markers of phishing emails
So, how can one recognize a message in their mailbox is a cyber attack attempt? There are some common markers you should look out for to identify a suspicious email:
- Non-typical sender. Never open mail from someone you don’t know or one you know but don’t expect to contact you. If anything you find suspicious, simply report it as spam.
- Incorrect sender’s email spelling. When getting a message from someone you trust (your team member, partner, or organization), pay attention to the email address. Once you notice a mismatch in at least one letter, don’t open it and report it as spam.
- Incredibly perfect text of the mail. If you did open the letter and find the message too good to be true, that’s 99% a scam. For example, the email states you won a prize or unexpectedly inherited a lot of money, so you must complete and sign documents using the attached link. Remember, it’s a trap — there is no such thing as a free lunch.
- A matter of urgency. Cybercriminals often urge quick action, claiming limited time to respond. Rushing you to update your account or personal details is also suspicious and should be ignored. Contact your service provider directly to verify such requests.
- Hyperlinks and attachments. Be careful with the website links you’re supposed to follow — any misspelling in the URL indicates a scam. Same with email attachments: don’t open them if anything looks unusual (like when, instead of a TXT or a PDF file, you get some strange format).
Some phishing statistics
To grasp the extent of risks posed by internet scams, let’s explore some statistics that reveal how even leading businesses fall victim to attackers.
- As per Cloudflare, mail attackers impersonate the top 20 global brands 51.7% of the time, with Microsoft being the most common.
- Sony fell victim to LinkedIn hackers who stole employee contacts, resulting in employees receiving malicious mail. This breach led to the loss of over 100 terabytes of business data and cost the company more than $100 million.
- In 2019, UK parliament members were targeted by a vishing attack, which involved the distribution of at least 21 million spam emails among UK lawmakers.
- There’s a report stating that generally new scam websites appears every 20 seconds.
These examples highlight the dangers of cyberattacks and demonstrate that even the most reputable businesses and organizations are vulnerable to breaches.
SignNow: A reliable service to sign your documents
Signing documents electronically is safer than traditional pen-and-paper signing processes. However, strict precautions are still required to exclude potential cyber threats and reputation damage. With SignNow, you can prevent phishing attacks and support your organization’s employees and customers with a dependable eSignature solution for any business transactions. Let’s see what makes SignNow so trustworthy for online document signing.
World-class security with SOC 2 Type II certified

With SignNow, our eSignature dependability is SOC 2 Type II Certified, which ensures complete security, availability, processing, confidentiality and privacy of your documents. SignNow maintains multiple document storage locations, so that your documents are always available and preserved. In addition, SignNow creates and maintains a detailed document history, which shows all document activity, to show you when, where, and how phishing attackers touched your documents.
Up-to-speed cyberattack prevention
At SignNow, we keep our employees informed about phishing attacks, and ways to combat malware techniques. By staying on top of new phishing techniques and keeping your eyes peeled for scams, you can spot phishing attempts as early as possible. For IT administrators, it’s highly recommended to organize regular data safety training sessions and keep employees up-to-date. If you’re looking for the latest technology and protective additional features to prevent phishing attacks, SignNow is your answer. If you’re looking for the latest technology and security features to prevent phishing attacks, SignNow is your answer.
Powerful anti-virus software
For SignNow, we use special anti-virus program to guarantee the highest protection for all forms you sign with an electronic signature. eSignatures that are included with anti-virus software combat cyberattacks and identity thefts. SignNow also keeps our software up-to-date, so that new scams can be combatted all the time – our updated anti-virus software is used to prevent phishing attacks anytime, anywhere.
Double-factor authentication
At SignNow, we have additional authentication and verification steps to secure your password, account, personal information, and important documents. Double-factor authentication is important to combat against sensitive requests, such as wire transfers. SignNow also has a policy to not send private or financially sensitive information about customers over email – SignNow employees also always check the address of an email or website, to make sure it’s safe.
Is SignNow trustworthy? Debunking user doubts
Electronic signature services, even the most secure and encrypted ones, are also at risk of malicious attacks. SignNow has established itself as a reliable solution for smooth electronic document signing, trusted by millions of users worldwide. Its robust data safety measures, including encryption and advanced authentication methods, ensure that documents and user data are always safe. However, the increasing sophistication of cybercriminals means users must remain vigilant about suspicious emails, even if they appear to be from someone they know. Let’s look into two real-life scenarios from Reddit on users getting dubious messages from our platform, reveal whether they were scams, and look at the actions you should take in similar situations.
Case study #1: Is an email invite for an online document signing a scam?
A while back, one user reported on Reddit the following situation: they received an email claiming to be an invitation to sign a document related to their work schedule using SignNow. They found the message generally fine but still a bit untrustworthy. What the user found suspicious was a generic greeting (not like those previously received from colleagues) and the sender’s name they saw for the first time.
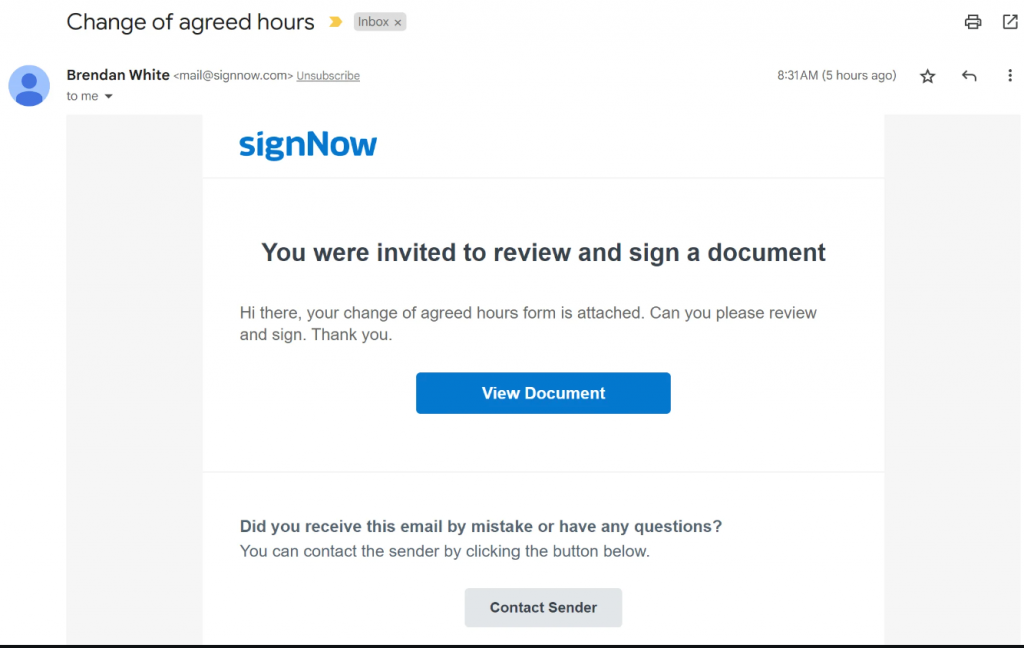
Upon closer examination, this email resembles a typical invite for signing. However, the signature request message deviates from SignNow’s default and appears poorly customized by the sender. Although the sender’s email indicates it’s from our platform (“@signnow.com”), and the primary concern lies in the identity of the individual requesting the signature.
Recommended actions
If you get in a similar situation, take these steps to safeguard your data:
- Don’t click on unfamiliar links until you ensure they’re safe. If you’re also registered with our solution, manually enter the SignNow website into your browser to access your account and check for pending documents. If you have no new pending forms, contact our support team.
- Verify the sender’s email address. Ensure it matches SignNow’s official domain. Genuine emails from SignNow come from a signnow.com domain.
- Cross-check with your employer. Since this email concerns work schedule changes, contact your employer or HR manager to confirm that there is a person with that name in your company. If not, report the issue to your IT department and our support specialists.
As we know from the forum discussion, the reported mail was from the user’s new colleague. To sum up, double-checking takes just a few extra minutes, but ignoring it may cost too much.
Case study #2: An email framed as if SignNow scams
Another Reddit user describes receiving an email appearing to be from SignNow, asking them to review and sign a new document. The email address it was sent from was “mail@signnow.com” and looked legitimate. However, the user noted inconsistencies such as an unfamiliar sender name, misspelled words, and a sense of urgency it conveyed, which set off alarm bells. Check the image below and see for yourself.
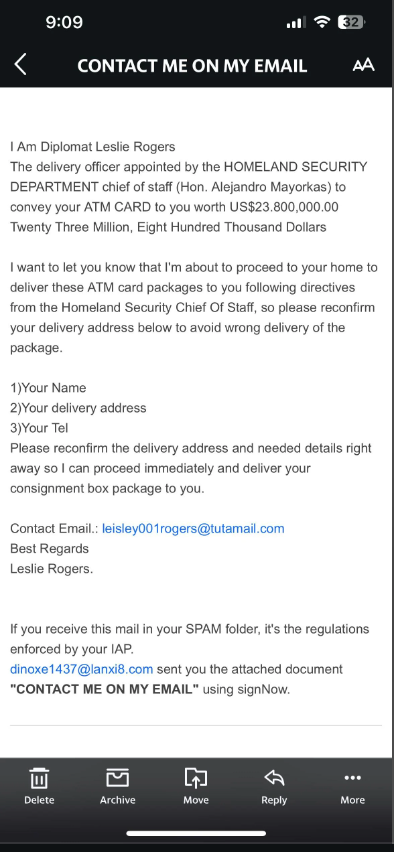
But it’s the context that reveals the scam in this mail—a supposed diplomat claiming to deliver a card valued at over twenty-three million dollars. That’s too good to be true, isn’t it?
Recommended actions
The described situation is a classic example of a scam. Once you get it, remember to carefully adhere to the following guidelines:
- Inspect email tone and language. Be wary of emails with poor grammar or spelling mistakes, as legitimate companies maintain professional communication standards.
- Check for urgency cues. Legitimate businesses won’t pressure you into immediate action. Be cautious of any email implying urgency.
- Notify the issue. Mark the message as spam and communicate with your company IT department or the SignNow support specialists about the case.
- Use double-factor authentication (DFA). Enable DFA for your SignNow account. Even if credentials are compromised, this adds an extra layer of security.
Final thoughts
Cybercriminals never stop inventing new ways to hook up your sensitive data and steal money. However, with vigilance and the right strategies, we can protect ourselves and maintain trust in our tools. By staying informed and proactive, we can enjoy the benefits of technology while keeping our systems secure.
Maintaining awareness and scrutinizing potentially suspicious emails are critical in safeguarding your digital information. If you have any uncertainties, always contact SignNow support from their official website to verify the authenticity of communications claiming to be from them. Stay secure and protect your data by practicing these simple yet effective preventive measures.
For more information about SignNow’s secure and world-class eSignature solution, visit SignNow’s corporate site.