In software development, ensuring secure, clearly implementable, and reliable communication between applications is paramount. An API, or Application Programming Interface, is an implementation or specification that enables a software system or module to be called in a standard way by other systems or modules. An API signature is a specific security and verification component of an API call.
APIs in context
Typically, an API has code that can be called in a special, documented way by an external service. An API call is often a single request to obtain or alter information, allowing the person invoking the API to incorporate the software’s functionality without understanding the inner workings of its code. APIs might internally face other parts of the same software system, or they might connect software created by different organizations.
A clearly documented and convenient-to-use API can make invocation of a service much more convenient. An internal API can be important for the development of a large codebase. An API available to external organizations can be an important product feature. The office workflow automation platform airSlate has multiple external APIs. The SignNow API supports automated sharing of legally binding agreements and other documents, for recipients to fill out and send.
Users of the SignNow and Document Automation Hub APIs can add pre-built features to fully automate key steps in the management of their documents, improving the efficiency of standard office processes. Access to airSlate’s APIs is commercially available.
What API signature means
Since it is open to being invoked by other software, including by potential attackers, an API must take precautions to remain secure. To ensure API use is authorized, potentially vulnerable API endpoints require authentication credentials. These credentials need to be properly encrypted if transmitted over the network.
The API signature is the component of the API call with the encrypted user credentials, which can be used to verify user authenticity and message integrity. It includes the user credentials encoded as a single encrypted string, possibly with other data, to be passed along with the rest of the API call.
It is standard and secure to pass these authentication credentials encoded using the 64-character Base64 encoding scheme. Base64 stores data as strings with an “alphabet” of 64 unique characters, with 6 bits for each character.
Two separate keys are used for encryption and decryption — the public and private keys. These are associated with one another and with a given user of the service. The private key — also known as the secret key — is used to encrypt the API signature and is stored securely by the holder.
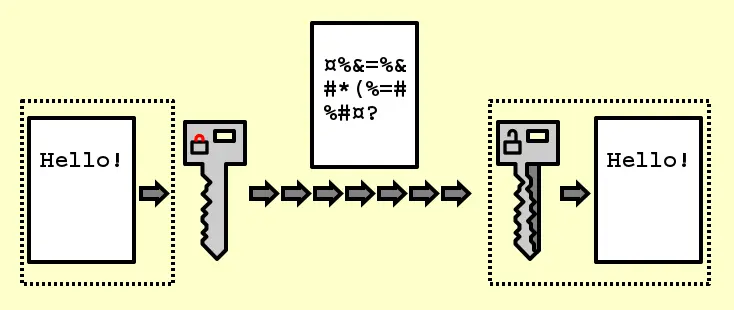
The public key of the key pair is publicly available. The API provider uses the public key associated with the user’s private key for decryption and verifies that the data is valid.
API signature example
The SignNow and Document Automation Hub APIs use API signatures to authenticate. Authentication is performed using a protocol called OAuth 2.0, in which user credentials — including public key and secret key — are obtained for each application and exchanged for access tokens. Correct access tokens, which take the form of character strings, are required for successful API calls.
Watch the video below for more information and insights on this topic:
Conclusion
API signatures use rigorous cryptographic methods to ensure that user credentials are correct and can pass over the network securely, and that the API provider can verify the message has not been corrupted. They help make it possible to use APIs to transmit highly sensitive private data.
In a more general context rather than specific to APIs per se, encryption and decryption using public and private keys is called digital signing.