Electronic signatures instill enough confidence that they have come to carry the legal weight of handwritten signatures. eSignatures are used in many official documents, from medical consent forms to legal contracts to government records, and are more convenient and traceable than manual signatures.
Numerous countries and the United Nations recognize and regulate their use. Laws vary regarding what security features are needed for eSignatures to be legally binding. Typically, they stipulate that the signatory can be uniquely identified and linked to the signature and that the signature is linked to the associated data so that subsequent changes to the data are detectable. The signature is only valid if its associated data has not been tampered with.
Technology has advanced to prevent forgery and tampering of eSignatures. Standard algorithms are used to encrypt and decrypt the signatures. eSignature algorithms sent over the network are generally based on what is known as public key cryptography.
Public and private keys
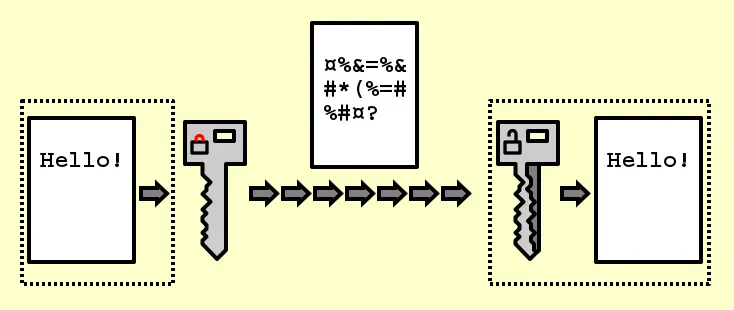
eSignatures use public key cryptography to verify that they have come from their supposed source and were not corrupted. A cryptographic key is a special piece of data, such as a large number or a sequence of characters, used to scramble data for security. Public key cryptography, also known as asymmetric cryptography, uses two separate keys for encryption: the public and private keys.
In public key cryptography, one key (public or private) encrypts the data, and the other decrypts it. The public key is publicly available. The private key — also known as the secret key — is stored securely by the holder.
In digital signing, a common cryptographic implementation of electronic signatures, the signer uses a private key for encryption. The recipient of the signed records uses the public key associated with the signer’s private key for decryption and verifies that the data is valid.
Encryption algorithms
Encryption over the network
Public key cryptography can work for as important a purpose as an eSignature. This is because, with the right algorithms, the encrypted messages are computationally impossible for hackers to decipher without the public and private keys. It is also computationally impossible to tamper with the public and private keys so corruption in messages goes unnoticed upon receipt.
Several algorithms have shown effectiveness for this purpose, and have become widely used for electronic signature encryption. Breaking their encryptions is thought to be prohibitively computationally inefficient. Hence, these algorithms are considered secure.
The eSignature service SignNow, a major eSignature application, uses multiple secure encryption algorithms in multiple contexts. It encrypts eSignatures using public and private keys in transport layer security (TLS), the cryptographic protocol for sending messages over a computer network. SignNow uses two algorithms for this purpose, since different browsers support different algorithms.
One is the popular RSA (Rivest–Shamir–Adleman) encryption algorithm. In the RSA algorithm, a public key is created based on the product of two large prime numbers and an auxiliary value. These numbers are kept secret.
There is no known method for factoring the product of large prime numbers efficiently, using a non-quantum computer. This is called the factoring problem. The RSA problem, the obtaining of an RSA private key given the public key, is not known to have an easier solution than factoring.
The other asymmetric encryption algorithm SignNow uses is the Elliptic Curve Digital Signature Algorithm (ECDSA). ECDSA is based on finding the logarithm of a random point within an elliptic curve.
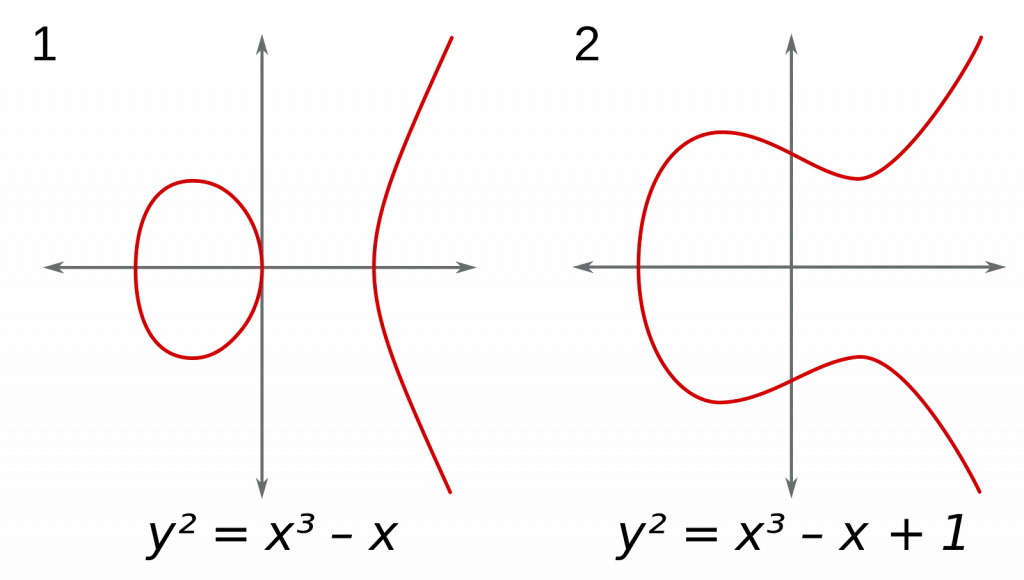
For comparable difficulty to crack, elliptic curve algorithms require smaller encryption keys than RSA algorithms. They are commonly used in cryptocurrency digital signature algorithms.
RSA and ECDSA are not the only encryption algorithms that can be used for digital signatures. The Digital Signature Algorithm (DSA) creates public and private keys based on raising a base digit to an exponent, dividing by a positive integer, and taking the remainder. Cracking this algorithm is based on computing the logarithm, a problem called the discrete logarithm problem that has yet to be known to have an efficient solution.
DSA decrypts and signs faster, making it more efficient server-side. However, RSA encrypts and verifies faster, making it more efficient for the client side. With clients of various capacities, including private individuals with limited computational resources, maximal client-side efficiency is key.
Encryption in the cloud
SignNow stores documents on an AWS S3 server, encrypting them as well as the keys used for asymmetric encryption. The S3 server uses Advanced Encryption Standard (AES) 256 encryption, which uses a single 256-bit key to encrypt and decrypt. An algorithm that uses the same key to encrypt and decrypt is called a symmetric encryption algorithm.
AES 256 encryption is the most secure type of AES encryption, and is prohibitively computationally expensive to crack. In this type of encryption, the data is divided into sections called blocks. Over multiple rounds of modification, the security keys determine how the blocks are scrambled. Using a predefined table, each byte of data is substituted for another byte. The same keys can unscramble the blocks.
Encrypted, the documents are far more difficult to hack should an attacker gain unauthorized access to the server.
Electronic signatures remain secure
Encryption of the signatures and of the documents containing them are only some of the security features of an electronic signature service. Encryption protocols for signatures are widely recognized and rigorously tested. Barring the existence of a quantum computer, they can be fortified to resist attacks effectively. For good reason, electronic signatures are a credible and trusted way to sign a document. As researchers delve into use cases for quantum computing, it’s crucial to consider how these developments might impact the strength of current encryption protocols.